
Out of all the criminal activities that occur daily, cybercrime is perhaps the most misunderstood. So much of it takes place behind closed doors, and it evolves and develops over time. It’s hard to keep track of what antivirus programs are currently the best choices, let along what they protect you from. The following assumptions about cybercrime aren’t as true as the media and CSI may have led you to believe, so keep that firewall turned on.
10. Cybercrime Is All About Hacking Data
The common mental image of a typical hacker goes along the lines of how Hollywood depicts them: a man furiously types away as the screen fills up with hundreds of lines of code at an unreadable rate. Then the hacker slams the Enter key, and the screen brings up a big green box that reads “Hack Successful.” That’s how all cybercrime goes down, right?
In fact, a lot of crime is committed without the criminal doing much at all. They wait for their victims to do the legwork. Everyone knows about the typical scams like phishing, fraudulent emails that demand user input. But not so much is known about the use of the Internet to commit robberies. Before you start wondering how criminals can climb through a computer screen and pop out in someone’s house, let’s look at a real world example.
Back in 2010, the police in the town of Nashua, New Hampshire broke up a robbery ring responsible for stealing up to US$200,000 worth of property. Their method? They monitored Facebook pages for people announcing holidays or other trips, then broke into the house when the owner wasn’t around. No amount of keeping the lights on would deter a robber from that offer. So when using the Internet, remember that crime goes a lot further than your firewall and antivirus. Keeping a smart head on your shoulders can go a long way.
9. We Can Regulate Illegal Downloads Easily
All this news about illegal downloads of games, music and movies doesn’t sound too bad in theory. All we have to do is find out who gives out downloads and shut them down. That will solve the problem, right?
Unfortunately, issues arise when you try to regulate the nature of illegal downloading. When someone downloads a file from someone else, they’re not taking the file from the other person - they’re duplicating it. This means it’s relatively easy to create a carbon copy of a file on an entirely different server, which is called a mirror. Criminals can use this to create backups should their primary server go down.
Okay, but what if the websites that list these illegal mirrors are blocked? Unfortunately, simply blocking websites doesn’t solve the problem. The Pirate Bay has been blocked in many countries, but people within said countries can still access the content through proxy services, which circumnavigate the block and deliver the content to the user. Blocking a website is easy, but keeping it blocked is like a virtual game of whack-a-mole that could end up being a 24/7 job for regulators.
8. Antivirus Software Block All Threats
Viruses and spyware can infect your computer and turn it into an attractive paperweight, but installing an antivirus program will lock down your computer and keep it safe, right?
Maybe a while ago, but modern developers of malicious software have adapted to how antivirus software works. An antivirus does its job by downloading a catalogue of virus definitions (imagine a row of mug shots of known criminal software). The antivirus then refers to this catalogue when scanning files and activity. The coders of these bad eggs have changed their strategy in response - instead of spreading one long-living virus which can be easily identified and deleted, they spread a wide range of viruses with short lifespans in an effort to beat the virus definitions.
How short lasting is the modern day virus? Fireeye states that 82 percent of viruses are designed to last only an hour. The result? 55 percent of cyber attacks go unnoticed by commercial antivirus software.
Before you pull the plug on your Internet connection and hide your computer in a nuclear bunker, it’s good to know that the best antivirus strategy is being knowledgeable about how to stay safe online. Sadly, this mean no more free kitten screensavers from strange foreign websites.
7. Microsoft Windows Is The Only Operating System With Viruses
This was one of the selling points for Apple products in the early days of the Internet. Windows machines were facing a slew of dangerous viruses, while other operating systems were spared. It seemed like the safer route to purchase a Mac or, ugh, install Linux.
The reason for this is two-fold. When creating a virus, you can only design it to target one family of operating systems. It makes sense to target the system that contains the most users, especially users with sensitive personal and commercial data. Given Windows’ spread around the world, it makes itself an appealing target. Macs are also based on UNIX, which has a solid security base.
However, Apple products have been under fire lately. Perhaps their growing popularity has led criminals to change targets, something the world witnessed during the Celebgate scandal when nude photos of various celebrities were stolen through iCloud. While the concept of Macs being safer than Windows is up for debate, there’s no arguing that Mac owners still need to take care with their data.
6. Big Businesses Are Totally Secure
Celebgate was a wake-up call to another misconception - just because a company is an expert in the computing field, it doesn’t mean they’re immune to cybercrime.
It’s easy to imagine big businesses having an impenetrable wall of firewalls, passwords and security experts. But while the scale of their security measures are probably very big, they’re by no means impenetrable. One particularly nasty case occurred when Sony was caught without up-to-date software. A hack against their PlayStation Network database managed to retrieve sensitive data like user payment details, and Sony ended up being fined just shy of US$400,000 for negligence.
5. Passwords Need To Be Mind-Bendingly Complex
You sit down to log onto a website. Hackers thought they could get into your account, but you’ve got one up on them - you’ve created a password so convoluted that not even a password cracker’s mind can comprehend it. Unfortunately, neither can yours. Was it N49Z@$2A, or N49Z@$2B?
Thankfully, the days of abysmally complicated passwords are over. One study showed that passwords that were minimum of eight characters were cracked 60 percent of the time when put up against a powerful piece of cracking software. 16 character passwords, meanwhile, only saw 12 percent of their passwords cracked.
What does this mean? It means that a password like ‘N49Z@$2A’ might be less secure than, say, ‘IC4nR3m3mb3rTh15’. The length of a password seems to be the winning factor, so a longer password that’s easy to remember will do more good than a short, complex password. It’s less frustrating and more secure at the same time - definitely a win-win for anyone but password crackers.
4. Only Criminals Are Hackers
We usually imagine hackers as a person or small group trying to break open the digital doors on valuable data. It may seem that all hackers are on the same level as virtual burglars, but it’s also an activity that governments partake in. Take, for example, the on-going cyber war between the United States and China. Relatively untouched by the news, both sides have been trying to take out chunks of each other’s digital infrastructures for years. In 2013, American spies hacked into China’s Tsinghua University. No one knows what they were looking for, but it probably wasn’t a course prospectus.
That’s just one example of many, and that’s just the activity that we know about from people admitting to it. Many more operations might be taking place right under our noses. As long as they don’t target cat videos on YouTube, they’ll continue to go relatively unnoticed.
3. Criminals Need Server Access To Do Damage
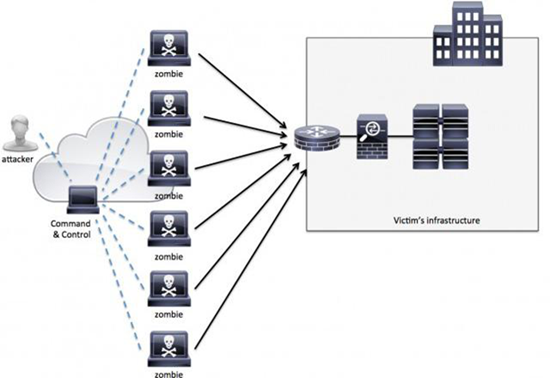
We’ve seen a lot of cases of people gaining unwanted access to servers and websites, but there are ways someone can attack a website without breaching any security. One method that’s seen a lot of use is the Direct Denial of Service (DDoS). A DDoS attack works by flooding a website with requests in a bid to take it offline. It’s like sending 1000 people into a McDonald’s to clog up the line and make bogus orders.
DDoS attacks are popular amongst those who want to make mischief or send a statement. LulzSec and Lizard Squad are examples of groups who wanted nothing more than to temporarily take down some of the biggest companies in the world for a laugh. But if DDoS attacks are performed on a store or other sales website, they can make a nasty dent in profits by preventing customers from making purchases. The punishments for DDoS attacks are quite severe, with the above groups already facing jail sentences.
2. All Contact From Friends Is Safe
Some old advice that went around the early days of the Internet was simply not to trust any communications that came from someone that you don’t know. Anyone you do know was 100 percent trustworthy, and it was fine to click anything they sent you. But criminals have managed to exploit this piece of advice for their own good. Knowing that a random stranger offering a link would be quickly blocked, people have taken to hijacking accounts and using them to message their friends and family with a link or a file to download. Given that it’s from a friend, it has to be trustworthy - and that’s when the virus hijacks their account too.
One virus takes over a Facebook account and sends a message to the account’s friends with a link claiming the friend has been spotted in a YouTube video. Once clicked, the target is told they need to download a plugin to see it. If the user downloads the plugin, it steals their Facebook and Twitter passwords, accesses their account and sends the message onwards. Always remember: if your otherwise prudent friend starts talking in vicious chat-speak and spams links at you, it’s probably not them anymore.
1. Criminal Websites Can Be Seen By Anyone
The news often reports of police shutting down specific criminal groups on the Internet. It must seem very easy - just type in a nefarious search term into Google, hit enter and arrest everyone who pops up. Unfortunately, most criminals (or at least the smart ones) can’t be found at all on Google. To locate them, you need to take a trip into the Deep Web.
The Deep Web itself isn’t a wholly bad thing. It just refers to webpages you can’t access directly through a Google search for various reasons. It takes up 90 percent of the Internet, but a lot of it is, say, administrative back end pages. However, this level of secrecy naturally lends itself to people who want to keep their online activities hush-hush.
Criminal websites on the Deep Web need more than a username and a password. You need a special browser to handle the specific connections needed to access the page, as well as encryption to ensure that your connection is untraceable. Users can then access web pages such as Silk Road, a website that sells drugs, weapons and other illegal goods. Like the Pirate Bay, authorities are having a hard time keeping Silk Road down, with alternatives popping up as soon as a previous version is shuttered. Unless you really feel the need to buy meth online, we wouldn’t recommend checking it out.









No comments:
Post a Comment
Please adhere to proper blog etiquette when posting your comments. This blog owner will exercise his absolution discretion in allowing or rejecting any comments that are deemed seditious, defamatory, libelous, racist, vulgar, insulting, and other remarks that exhibit similar characteristics. If you insist on using anonymous comments, please write your name or other IDs at the end of your message.