
Five Facebook Threats That Can Infect Your PC, And How They Work
By Kihara Kimachia, Make Use Of, 1 September 2014.
By Kihara Kimachia, Make Use Of, 1 September 2014.
Do you remember how life was without Facebook? Probably not. The site has pervaded our lives and it is no surprise that Facebook is now prime hunting ground for anyone with nefarious intentions.
They employ stealth and cunning, like a predator stalking its prey, looking for the slightest weakness to pounce on you. By simply visiting Facebook, you potentially expose yourself to viruses and malware. Criminals can make you take some unintended action, steal your data, spy on you or “enslave” your PC for their own illegal ends such as launching DDOS attacks.
We take you through some of these Facebook threats and outline the precautions you should take to avoid becoming another statistic of cyber crime.
1. Clickjacking Threats
Clickjacking is one of the oldest tools used by scammers on the Internet and most common ingredient to all other threats listed below. Users are tricked, using psychological manipulation, into clicking links that do something totally different from what the user expects them to do. This is achieved by overlaying legitimate Facebook pages with malicious content from a third party site. For example, you may click on a button that is supposed to take you to a specific page but instead the action enables your webcam.
On Facebook and other social media websites, clickjacking has been employed in a variety of ways. For example, “likejacking”, a variation of the clickjack, is a malicious technique that tricks users into unintentionally “liking” a page. Clickjacking on Facebook has also been used to infect users’ computers with malicious code. Once you click a malicious link, you unwittingly download malware to your computer. Some of the techniques used in recent clickjacking attacks include:
Breaking News - this could range from gossip to entertainment and will typical be controversial or intriguing to attract curiosity and ultimately get you to click the link. For example, celebrity death hoaxes.
Exclusive Content - these attacks come with statements promising access to exclusive videos or photos. Again, the content will be controversial or intriguing.
Latest News - this attack takes advantage of the latest trending news and takes advantage of the basic human instinct to want to stay updated in real-time with an on-going news event.
Promos/Contests - this attack entices users with a great promotion or contest. Users are asked to click a link in order to register for the promo or contest.
Precautions
Facebook continues to implement site updates to protect their users from clickjacking but there are a few ways you can proactively avoid the threat. To begin with, avoid clicking on links in your Facebook feed; if it’s too good to be true, it probably is.
Also, some headlines are dead giveaways that something is off. Be wary of catchy headlines you know can’t possibly be true, for example, “[RAW UNCUT VIDEO] MERMAID WASHES UP OFF COAST OF FLORIDA.” Seriously, if you click on such a link, you’re asking for it.
You should also restrict your Facebook contacts to people you know personally and make your Facebook profile private. Don’t click on news links whose source appears dodgy; for breaking and latest news, read credible news sites.
Be a good net citizen and help out the community by proactively reporting suspicious sites to Facebook admin. If you are using the Firefox browser, install the free NoScript add-on. Its Clear Click feature offers reasonable protection against clickjacking. Finally, install antivirus software that offers complete Internet security.
2. Phishing Exploits
A phishing attack is the online version of impersonation. The attacker masquerades as a trustworthy entity. For example, you may be presented with a Facebook login portal that looks like the real thing. Once you enter your username and password, you essentially hand over your Facebook account to the attacker.
One of the most recent common phishing attacks is a bogus application used to steal login credentials. You may have seen reports in 2013 of an app that boasted it could enable users to see who had viewed their Facebook profile. The site spoofed the appearance of Facebook’s login page and offered two options to activate the fake app. The first option asked users to enter their credentials into the fake website while the second option asked users to download and install software in order to receive notifications when someone viewed their profile. This software was in fact malware that would set up a keylogger on the victim’s computer and send the logged data to phishers as soon as an Internet connection was detected.
Precautions
One of the most basic ways to prevent a phishing attack is to check the URL in the address bar to be sure you are actually entering your login credentials in the genuine Facebook login page and not a spoof. Also, look for the padlock icon to ensure it is a secure page (https) and if you’re not sure, click on the padlock icon to confirm the site’s identity is verified as Facebook.com. Take this a step further and ensure you are using the latest generation of web browser; make sure you update your browser on a regular basis. Chrome, Firefox, IE and Opera all come with built-in phishing and malware protection. For added security, check out these three browsers designed to protect your privacy.
Don’t click on Facebook links that promise something new or unusual before confirming the same with reputable websites. For example, in the phishing attack described above, all a potential victim needed to do was find out if “see who viewed your profile” was possible by posting a question on a reputable site like Make Use Of.
You may also want to check out a new app known as Fakeoff. Fakeoff uses an algorithm to detect if a user’s profile is fake. It analyzes profile information and even checks to see if the profile photos are fake.
3. The “Facebook Team”
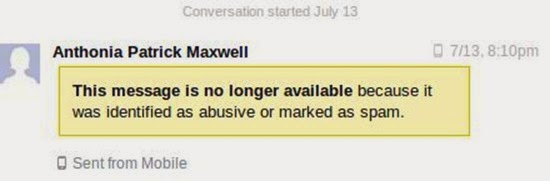
This attack also employs impersonation. The attacker sends you a message while posing as Facebook admin or customer support. A typical message will ask you to take some action urgently, for example, clicking on an attachment or link to update your account or to respond to a query. The links lead to malware sites and any attachments are packaged with malware that infects your PC.
Another variation of the “Facebook Team” threat is a fake invite that offers a prize if you forward it to all your friends or post content (spam) on their walls. Fake pages can also be set up as front for clickjacking pr phishing schemes. One such example is iBanking, a malicious Android app designed for e-banking fraud and specifically to bypass the two-factor authentication feature used by banks. Users are lured into installing the app on their phones through JavaScript injected into Facebook web pages. The content shown in the screen capture above appears on the webpage.
Precautions
Credit: Laurel L. Ruswwurm/Flickr
This calls for a bit of good sense and sound judgement on your part. Facebook has strict anti-spam rules so it stands to reason that they will not ask you to spam other people. Also, many messages purportedly from Facebook are normally written in poor grammar or contain subtle grammatical errors (see the screen shot above) that should trigger alarm bells.
If you receive a suspicious message from the “Facebook Team,” delete it immediately without clicking anything and report the user to Facebook.
4. Rogue Facebook Applications
Are you an avid fan of Candy Crush Saga, Family Heroes and other Facebook games? Apps are common targets for clickjacking, malware and phishing. Rogue apps look like the real thing and people click “Allow” without thinking twice about it. Before you know it, your Facebook account has been hijacked and used to spread spam to all your friends. Some apps also carry out “tag-jacking” where a photo tagging exploit is used to spread spam on Facebook.
Precautions
Spotting a rogue app can be rather difficult because they are engineered to look as much as possible like the real deal. The best way to avoid a rogue app is to avoid third-party applications entirely. However, this may be a bit extreme to some people and may mean not getting their daily gaming fix. The more practical approach is to be very selective about the applications you install. Stick with well known developers and always carry out extensive research before allowing an app access to your Facebook account.
Also, re-check the list of applications you have allowed access to your account by going to the arrow down link at the top right of your Facebook page. Scroll down, click Settings > Apps. Review the permissions of apps you are currently using and delete any you aren’t too sure about. As a general rule, steer clear of any apps that request total access to your Facebook account, access to your chat messages and the right to manage pages and events. Spammers need access to the latter two to effectively spam your entire network.
To prevent “tag-jacking”, go to Timeline and Tagging > Tag Review and enable Review posts friends tag you in before they appear on your timeline.
5. Malware Attacks
Credit: JMiks/ShutterStock
Malware and viruses can be injected into your computer via Facebook using any of the methods listed above. Recent malware attacks propagated using Facebook include:
Zeus - this is a Trojan horse that attacks Windows computers. After clicking a link, it downloads itself to your computer and remains dormant until someone triggers its activation - in this case, attempting to log into a bank account acts as the trigger. Once that happens the virus comes alive and swipes user names and passwords. The attacker can then retrieve this information remotely and take you to the cleaners.
The Koobface attack also uses clickjacking to infect users computers. The attack usually arrives as a private message or status update from the user’s friends. Clicking on the messages or updates leads to a site (usually a fake YouTube site) with a hosted video. The play button launches a fake Adobe Instant player executable file, which is really a downloader of the Koobface components.
“LOL” Virus - The “Lol” virus spreads through Facebook’s chat function. Users receive a message from one their friends simply stating “lol” and with an attachment. Curious, they click the attachment which triggers the download of a Java file containing malware from Dropbox. The virus infects the computer and hijacks your Facebook account and spreads itself to your network of friends.
Precautions
New threats are coming up everyday but a good way to avoid malware is not to click chat message links from people that aren’t your friends. Update your privacy settings so that you can’t receive such messages. More specifically, Zeus targets Windows users leaving Mac and Linux users unaffected. So, while avoiding Windows altogether may not be a sensible solution, you may consider using a different desktop operating system to access Facebook where possible.
As for the “Lol” virus, be on the lookout for messages that simply contain the words “lol” and an attachment. If unsure a message is from one of your friends, pick up the phone and call them or send an email.
Windows users should also ensure they have a good antivirus and once again, it is imperative to keep your browser up-to-date.
Eternal Vigilance!
Almost all the threats described above require the user to be careless in some way in order for an actual attack to take place. The best advice that anyone can give you about Facebook and other social media sites is to be vigilant and keep a healthy level of paranoia at all times. Also, Facebook is constantly on the lookout for new exploits and immediately notifies users. To receive regular security updates in your Facebook feed, like the Security Page.








No comments:
Post a Comment
Please adhere to proper blog etiquette when posting your comments. This blog owner will exercise his absolution discretion in allowing or rejecting any comments that are deemed seditious, defamatory, libelous, racist, vulgar, insulting, and other remarks that exhibit similar characteristics. If you insist on using anonymous comments, please write your name or other IDs at the end of your message.