
12 surprising ways personal technology betrays your privacy
By Andy Patrizio, IT World, 30 September 2014.
By Andy Patrizio, IT World, 30 September 2014.
It's not just your boss or the government that's spying on you, it's also the devices and technologies you embrace.
Our great privacy fears tend to be centred around others invading out privacy, whether it's Google reading your email, your boss monitoring your computer use, or the NSA eavesdropping on phone calls.
The problem is, we don't think about the very technologies we voluntarily embrace and what kind of snooping they do, and they do a lot of tracking. Some of it can and is used for benign or helpful reasons, but that can be turned against you very fast.
Here are 12 ways your personal technology is betraying your privacy.
1. Smartphone cameras spying on you
A computer science student in the UK recently published a blog post where he showed how you can create an Android app that can stay hidden from your app list and will take photos with your phone without you knowing it.
Szymon Sidor claimed that his Android app works by using a tiny preview screen measuring just 1 pixel x 1 pixel. According to Sidor, the Android operating system won't allow the camera to record without running a preview, so he made a preview app of one pixel, making it pretty much invisible to the naked eye.
Allowing the camera to run in the background without any indication it is running should be fixed by Google, Sidor said in his blog post.
2. Factory resets don't wipe your phone
If you are about to turn in or hand down your old smartphone, you do a factory reset and everything is wiped clean, right? Well, no.
Antivirus firm Avast probed several Android phones that had been factory reset and managed to recover more than 40,000 photographs, the identities of four previous owners, one completed loan application, more than 250 contact names and email addresses, more than 750 emails and text messages, and more than 1,000 Google searches.
Like on PCs, the mobile OS deletes the corresponding pointers in the file table and marks the space occupied by the file as free. Eventually, the file is expected to be overwritten, but until it is, the file is still present and thus recoverable.
3. Your phone spills details
When the National Security Agency's mass surveillance of telephone calls was first exposed, the agency argued that it was merely collecting metadata - the phone numbers of the caller and recipient - and not all kinds of personal information. Two Stanford University computer science students proved that wrong.
They showed they were able to acquire much more detailed information about people's lives from metadata than previously assumed possible. They were able to find the particular serial number of the phones involved, the time and duration of calls and possibly the location of each person when the call occurred.
4. Your browser gives away your history
Browsers have become much more secure, but not entirely. At the 2014 RSA Security Conference, RSA presented a discussion titled "Is Your Browser a User Agent or a Double Agent?" The problem, RSA noted, is that Web browsers have a wide range of sensitive data and user behaviour, any or all of which may be cached or captured by the browser or monitored via third-party cookies within the browser.
The problem centres around targeted ads. Rather than just displaying random ads that may or may not appeal to you, sites will rummage through your history and cookies to learn your online behaviour to target ads that are more likely to pique your interest.
5. You can be profiled by Facebook Likes
Do you have a Facebook friend who "Likes" virtually everything you post? Well, they are giving away basically everything about themselves to Facebook.
Research published in the journal PNAS (Proceedings of the National Academy of Sciences) shows that Facebook can draw very accurate profiles of a user's race, age, IQ, sexuality, personality, substance use and political views from automated analysis of only their Facebook Likes.
Researchers at Cambridge’s Psychometrics Centre and Microsoft Research Cambridge analyzed a dataset of over 58,000 U.S. Facebook volunteers. Models were 88% accurate in determining male sexuality, 95% accurate in distinguishing African-Americans from whites and 85% accurate differentiating Republican from Democrat. Christians and Muslims were correctly identified in 82% of cases, relationship status and substance abuse were predicted 65% and 73%.
6. Your GPS knows where you've been
GPSes are a lifesaver for drivers. You can find the closest gas station or restaurant or simply hit the Go Home button and it will get you out of wherever you are. But they also know where you've been - and for quite some time.
My Garmin GPS keeps more than two weeks of daily travel patterns in its history, and I never knew this until discovering the history by accident. It had the route for each day and every stop, with how long I was at each stop. Garmin also keeps a history of your recent searches, so if you want to return to a place you've already been, it will be in the search history.
7. Secret isn't so secret
There is an app called Secret that lets people confess to everything from minor infractions to major happenings in their lives. People make some occasionally shocking confessions on Secret, and others can comment and respond. All of it perfectly anonymous.
Well, not so much, according to Wired. Late last month, two white hat security hackers announced they had found a way to read the personal info of everyone sending their confessions to Secret.
For now, it's been fixed. But be warned: Anonymous confessional apps like PostSecret, Whisper, and Yik Yak may not protect your identity.
8. Chicago's lamp posts are watching
In my first story on privacy-shredding technologies, I introduced you to street lamps that would record conversations. Now, the city of Chicago is adopting something similar.
The Tribune reports that devices going up on Michigan Avenue, the iconic street that's a tourist trap and the scene of many movies, will have artistic decorative metal ornaments housing data-collection sensors that will measure air quality, light intensity, sound volume, heat, precipitation and wind. They will also count people by measuring wireless signals on mobile devices.
Scanning every smartphone that walks by? No potential for abuse there, especially when we have mystery cell phone towers popping up all over the country and no one knows who owns them.
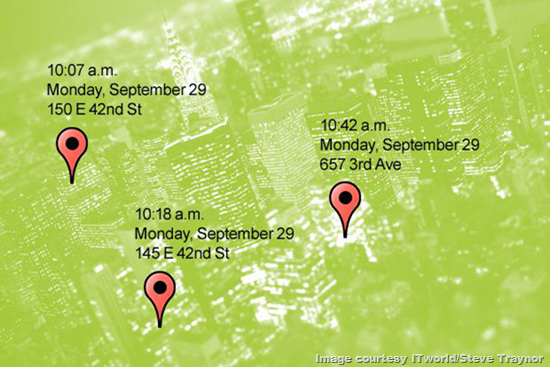
9. Google Maps on Android is following you
Let's face it, Google already knows a lot about its Chrome and Gmail users, so this shouldn't come as a shock. If you run Google Maps on your Android phone, it tracks all of your movement and retains a history of activities, broken down by date and where you were throughout the day.
Android users, just go to this page and see your movements over the last few weeks, which shows your movements sequentially and at what time (first reported by TechCrunch in December 2013).
It is possible to turn this off. In your Android phone, go to Settings, then Location, select Google Location Reporting and set Location History to off.
10. LG makes you choose: your privacy or your Smart TV
In my first piece I noted that a Smart TV from Korean vendor LG was caught spying on its owner. Now LG is outright demanding the ability to do it.
A reader wrote to TechDirt that because he refused to agree to LG's Privacy Policy, he can no longer access any of the TV's network based programs.
LG makes it very clear: "You do not have to agree to the Privacy Policy but if you do not, not all Smart TV Services will be available to you."
11. Electric smart meters know when no one's home
Users aren't really embracing smart meters, but the electric companies are. The smart readers make meter-reading easy by sending out a signal that is captured by a device carried by the meter reader.
The problem with these things is twofold: First, they send out signals regularly, not just when a meter reader is in the area. Second, that the signal is usually unencrypted. So anyone who hacks (or steals) a meter reading device can see when power usage drops, perhaps indicating that no one is home.
And it's not like the bad guys need to be in your yard. In 2012, a university professor found he could read unencrypted signals from 300 meters, or almost 1000 feet away.
12. Twitter and Instagram: giving away your location every time
Most people don't realize Twitter and Instagram both use geotagging for everything you send out. Geotagging is storing your latitude and longitude of your tweet or image. In fact, geotagging may have given away a major world controversy.
Last July, a bored Russian soldier began posting a string of selfies at work, and since he had turned on adding photos to maps when posting images to Instagram, his location was added as well. One featured him on a Buk anti-aircraft missile launcher, the kind used to shoot down Malaysian Airlines Flight 17. His geotagging information revealed he was inside the Ukraine, even when Russian President Vladimir Putin was denying soldiers were in Ukraine.
All images courtesy of ITworld/Steve Traynor.








No comments:
Post a Comment
Please adhere to proper blog etiquette when posting your comments. This blog owner will exercise his absolution discretion in allowing or rejecting any comments that are deemed seditious, defamatory, libelous, racist, vulgar, insulting, and other remarks that exhibit similar characteristics. If you insist on using anonymous comments, please write your name or other IDs at the end of your message.